购物宝典+脱单秘籍?当心病毒攻击
【文章摘要】 2017年11月8、9平安舆情:安卓恶意软件,新诓骗样本,重大破绽,其他平安事宜等黑客攻击尼泊尔银行的SWIFT服务器
https://www.bankinfosecurity.com/report-attackers-hacked-nepalese-banks-swift-server-a-10437

威胁组织APT28将Office恶意软件纳入引用NYC恐怖袭击的文档中
https://securingtomorrow.mcafee.com/mcafee-labs/apt28-threat-group-adopts-dde-technique-nyc-attack-theme-in-latest-campaign/#sf152439567
BROTHER打印机易受远程拒绝服务攻击
https://threatpost.com/brother-printers-susceptible-to-remote-denial-of-service-attacks/128790/

GOOGLE修补了ANDROID中的KRACK破绽
https://threatpost.com/google-patches-krack-vulnerability-in-android/128818/

赛门铁克的恶意软件研究人员发现了一个新的网络间谍活动APT,被称为Sowbug团体,至少自2015年以来一直活跃
http://securityaffairs.co/wordpress/65293/apt/sowbug-group-apt.html

GIBONRansomware在俄罗斯的漆黑网络论坛上售价500美元
https://www.scmagazine.com/gibon-ransomware-delivered-via-malspam/article/705727/
网购诈骗套路翻新 如何安全“避坑”
Payment&Shipping文档malspam通过未知的RTF破绽提供Lokibot和其他恶意软件
https://myonlinesecurity.co.uk/second-part-payment-shipping-documents-malspam-delivers-lokibot-and-probably-other-malware-via-an-unknown-rtf-exploit/

OilRig团伙在最近的攻击中使用了一款名为"ALMACommunicator"的基于DNSTunneling的木马
https://researchcenter.paloaltonetworks.com/2017/11/unit42-oilrig-deploys-alma-communicator-dns-tunneling-trojan/

GooglePlayStore中发现几款加密钱币挖矿APP
https://www.ixiacom.com/company/blog/everythings-better-blockchain

微软发了一份通告,指引用户若何防御OfficeDynamicDataExchange(DDE)攻击
https://technet.microsoft.com/library/security/4053440
挟制Windows系统数字签名的PowerShell剧本
https://pentestlab.blog/2017/11/08/hijack-digital-signatures-powershell-script/
发现隐藏在伪造的Flash更新中的连续威胁
https://zhuanlan.zhihu.com/p/30834498
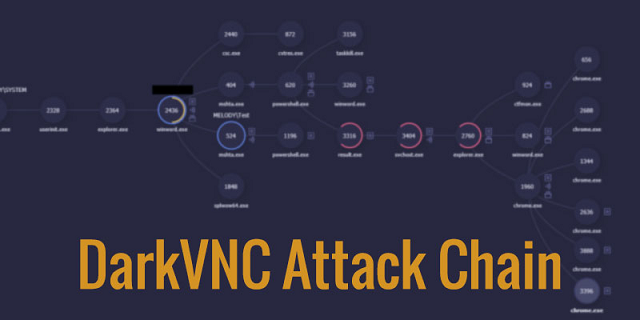
针对DarkVNC攻击链的简朴剖析
https://reaqta.com/2017/11/short-journey-darkvnc/
伪勒索病毒:劫财又“撕票”?